| Version | Date | Author | Comments |
|---|---|---|---|
| 2.0.0 draft-0.0.1 | Open Banking Read/Write API Team | This is the initial draft version. | |
| 2.0.0 draft-0.0.2 | Open Banking Read/Write API Team | Updated draft. | |
| 2.0-draft-3 | Open Banking Read/Write API Team | Updated draft. Removed all common elements | |
| 2.0-rc1 | Open Banking Read/Write API Team | Incorporate PCA and BCA Data model changes Account type related changes | |
| 2.0-rc2 | Open Banking Read/Write API Team | Account and Transaction Info API restructure. Section 4.6 - Removed rate limiting, and clarification on behaviour. Updates:
| |
| 2.0-rc3 | Open Banking Read/Write API Team | This is the initial draft version for rc3 Updates:
| |
| 2.0.0 | Open Banking Read/Write API Team | This is the baseline version. No changes from v2.0-rc3. |
This specification describes the Account Information and Transaction API flows and payloads.
The API endpoints described here allow an Account Information Service Provider ('AISP') to:
This specification should be read in conjunction with Read/Write Data API Specification v2.0 which provides a description of the elements that are common across all the Read/Write Data APIs.
This document consists of the following parts:
Overview: Provides an overview of the scope of the API and the key decisions and principles that contributed to the specification.
Basics: The section identifies the resources, operations that are permitted on those resources, and various special cases.
Endpoints: Provides the list of endpoints for the API specification. The individual end-points are documented in seperate pages along with the data model that the employ and usage examples.
Security & Access Control: Specifies the means for AISPs and PSUs to authenticate themselves and provide consent.
Data & Payloads: Documents data structures and data architecture that applies to all the end-points. End-point specific data structures are documented in seperate pages along with the end-points that employ the data structure.
Swagger Specifications: Provides links to the swagger specifications for the APIs.
The APIs specified in this document provide the ability for AISPs to access a PSU's account and transaction information for domestic PSD2 in-scope accounts.
The only resource that specifically relates to the CMA Order is the products resource - with the BCA and PCA objects. All other resources are driven by PSD2 requirements.
This Account and Transaction Info API specification does not cater for:
The figure below provides a general outline of an account information requests and flow using the Account Info APIs.

Step 1: Request Account Information
Step 2: Setup Account Request
Step 3: Authorise Consent
Step 4: Request Data

participant PSU
participant AISP
participant ASPSP Authorisation Server
participant ASPSP Resource Server
note over PSU, ASPSP Resource Server
Step 1: Request account information
end note
PSU -> AISP: Get account/transaction information
note over PSU, ASPSP Resource Server
Step 2: Setup account request
end note
AISP <-> ASPSP Authorisation Server: Establish TLS 1.2 MA
AISP -> ASPSP Authorisation Server: Initiate Client Credentials Grant
ASPSP Authorisation Server -> AISP: access-token
AISP <-> ASPSP Resource Server: Establish TLS 1.2 MA
AISP -> ASPSP Resource Server: POST /account-requests
ASPSP Resource Server -> AISP: HTTP 201 (Created), AccountRequestId
AISP -> PSU: HTTP 302 (Found), Redirect (AccountRequestId)
note over PSU, ASPSP Resource Server
Step 3: Authorise consent
end note
PSU -> ASPSP Authorisation Server: Follow redirect (AccountRequestId)
PSU <-> ASPSP Authorisation Server: authenticate
PSU <-> ASPSP Authorisation Server: SCA if required
PSU <-> ASPSP Authorisation Server: select accounts
ASPSP Authorisation Server -> PSU: HTTP 302 (Found), Redirect (authorization-code)
PSU -> AISP: Follow redirect (authorization-code)
AISP <-> ASPSP Authorisation Server: Establish TLS 1.2 MA
AISP -> ASPSP Authorisation Server: Exchange authorization-code for access token
ASPSP Authorisation Server -> AISP: access-token
note over PSU, ASPSP Resource Server
Step 4: Request data
end note
AISP <-> ASPSP Resource Server: Establish TLS 1.2 MA
AISP -> ASPSP Resource Server: GET /accounts
ASPSP Resource Server -> AISP: HTTP 200 (OK), List of accounts containing AccountId(s)
AISP -> ASPSP Resource Server: GET /accounts/{AccountId}/transactions
ASPSP Resource Server -> AISP: HTTP 200 (OK), List of transactions
|
The API endpoints for creating account-request resources are not idempotent.
If a time-out error occurs - then we would expect an AISP to create a new account-request resource - rather than try with the same resource.
This section looks at the list of available API endpoints to access Account Information and Transaction data and optionality (definitions of mandatory, conditional or optional are defined in the Principles section).
If an ASPSP has not implemented an API endpoint, it must respond with a 404 (Not Found) for requests to that URL.
Endpoint design considerations:
We have specified the "mandatory" endpoints for the functioning of the Account Info APIs.
However, endpoints will be not be "mandatory" if ASPSPs do not provide these resources via existing online channels - e.g., direct debits, standing orders, statements.
The access tokens required for accessing the Account Info APIs must have at least the following scope:
accounts |
AISPs must use a client credentials grant to obtain a token to access the account-requests resource.
AISPs must use an authorization code grant to obtain a token to access all other resources.
The AISP must create an account-request resource through a POST operation. This resource indicates the consent that the AISP claims it has been given by the PSU to retrieve account and transaction information. At this stage, the consent is not yet authorised as the ASPSP has not yet verified this claim with the PSU.
The ASPSP responds with an AccountRequestId. This is the intent-id that is used when initiating the authorization code grant (as described in the Trust Framework).
As part of the authorization code grant:
Once these steps are complete, the consent is considered to have been authorised by the PSU.
The Account Request resource consists of the following fields, which together form the elements of the consent provided by the PSU to the AISP:
Permissions codes will be used to limit the data that is returned in response to a resource request.
When a permission is granted for a "Detail" permission code (e.g., ReadAccountsDetail), it implies that access is also granted to the corresponding "Basic" permission code (e.g., ReadAccountsBasic)
The permissions array must contain either ReadAccountsBasic or ReadAccountsDetail.
The following combinations of permissions are not allowed, and the ASPSP must reject these account-requests with a 400 response code:
| Permissions | Endpoints | Business Logic | Data Cluster Description |
|---|---|---|---|
| ReadAccountsBasic | /accounts /accounts/{AccountId} | Ability to read basic account information | |
| ReadAccountsDetail | /accounts /accounts/{AccountId} | Access to additional elements in the payload | Ability to read account identification details |
| ReadBalances | /balances /accounts/{AccountId}/balances | Ability to read all balance information | |
| ReadBeneficiariesBasic | /beneficiaries /accounts/{AccountId}/beneficiaries | Ability to read basic beneficiary details | |
| ReadBeneficiariesDetail | /beneficiaries /accounts/{AccountId}/beneficiaries | Access to additional elements in the payload | Ability to read account identification details for the beneficiary |
| ReadDirectDebits | /direct-debits | Ability to read all direct debit information | |
| ReadStandingOrdersBasic | /standing-orders /accounts/{AccountId}/standing-orders | Ability to read basic standing order information | |
| ReadStandingOrdersDetail | /standing-orders /accounts/{AccountId}/standing-orders | Access to additional elements in the payload | Ability to read account identification details for beneficiary of the standing order |
| ReadTransactionsBasic | /transactions /accounts/{AccountId}/transactions | Permissions must also include at least one of:
| Ability to read basic transaction information |
| ReadTransactionsDetail | /transactions /accounts/{AccountId}/transactions | Access to additional elements in the payload Permissions must also include at least one of
| Ability to read transaction data elements which may hold silent party details |
| ReadTransactionsCredits | /transactions /accounts/{AccountId}/transactions | Access to credit transactions. Permissions must also include one of:
| Ability to read only credit transactions |
| ReadTransactionsDebits | /transactions /accounts/{AccountId}/transactions | Access to debit transactions. Permissions must also include one of:
| Ability to read only debit transactions |
| ReadStatementsBasic | /statements /accounts/{AccountId}/statements | Ability to read basic statement details | |
| ReadStatementsDetail | /statements /accounts/{AccountId}/statements/{StatementId}/file | Access to additional elements in the payload Access to download the statement file (if the ASPSP makes this available). | Ability to read statement data elements which may leak other information about the account |
| ReadProducts | /products /accounts/{AccountId}/product | Ability to read all product information relating to the account | |
| ReadOffers | /offers /accounts/{AccountId}/offers | Ability to read all offer information | |
| ReadParty | /accounts/{AccountId}/party | Ability to read party information on the account owner. | |
| ReadPartyPSU | /party | Ability to read party information on the PSU logged in. | |
| ReadScheduledPaymentsBasic | /scheduled-payments /accounts/{AccountId}/scheduled-payments | Ability to read basic statement details | |
| ReadScheduledPaymentsDetail | /scheduled-payments /accounts/{AccountId}/scheduled-payments | Access to additional elements in the payload | |
| ReadPAN | All API endpoints where PAN is available as a structured field | Request to access to PAN in the clear | Request to access PAN in the clear across the available endpoints. If this permission code is not in the account-request, the AISP will receive a masked PAN. While an AISP may request to access PAN in the clear, an ASPSP may still respond with a masked PAN if:
|
The additional elements that are granted for "Detail" permissions are listed in this section.
All other fields (other than these fields listed) are available with the "Basic" Permission access.
| Permission - Detail Codes | Data Element Name | Occurrence | XPath |
|---|---|---|---|
| ReadAccountsDetail | Account | 0..1 | OBReadAccount2/Data/Account/Account |
| ReadAccountsDetail | Servicer | 0..1 | OBReadAccount2/Data/Account/Servicer |
| ReadBeneficiariesDetail | CreditorAgent | 0..1 | OBReadBeneficiary2/Data/Beneficiary/CreditorAgent |
| ReadBeneficiariesDetail | CreditorAccount | 0..1 | OBReadBeneficiary2/Data/Beneficiary/CreditorAccount |
| ReadStandingOrdersDetail | CreditorAgent | 0..1 | OBReadStandingOrder2/Data/StandingOrder/CreditorAgent |
| ReadStandingOrdersDetail | CreditorAccount | 0..1 | OBReadStandingOrder2/Data/StandingOrder/CreditorAccount |
| ReadTransactionsDetail | TransactionInformation | 0..1 | OBReadTransaction2/Data/Transaction/TransactionInformation |
| ReadTransactionsDetail | Balance | 0..1 | OBReadTransaction2/Data/Transaction/Balance |
| ReadTransactionsDetail | MerchantDetails | 0..1 | OBReadTransaction2/Data/Transaction/MerchantDetails |
| ReadTransactionsDetail | CreditorAccount | 0..1 | OBReadTransaction2/Data/Transaction/CreditorAccount |
| ReadTransactionsDetail | DebtorAccount | 0..1 | OBReadTransaction2/Data/Transaction/DebtorAccount |
| ReadStatementsDetail | StatementAmount | 0..* | OBReadStatement1/Data/Statement/StatementAmount |
| ReadScheduledPaymentsDetail | CreditorAgent | 0..1 | OBReadScheduledPayment1/Data/ScheduledPayment/CreditorAgent |
| ReadScheduledPaymentsDetail | CreditorAccount | 0..1 | OBReadScheduledPayment1/Data/ScheduledPayment/CreditorAccount |
In addition the ReadStatementsDetail is required to access the statement file download via: /accounts/{AccountId}/statements/{StatementId}/file
Example behaviour of the Permissions for the ReadAccountsBasic and ReadAccountsDetail codes is as follows:
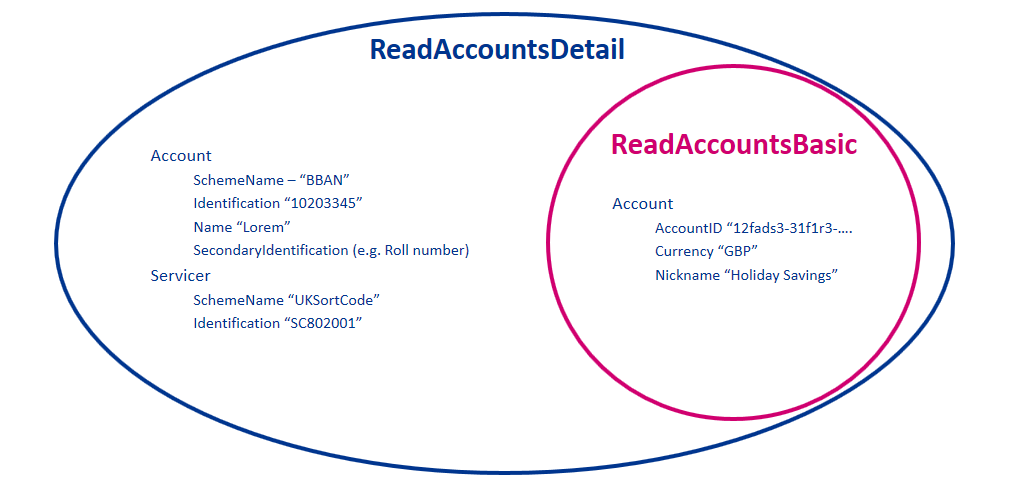
It is expected that transactions will be returned in the payload irrespective of whether they are reversing entries as long as the PSU has provided consent for that type of transaction.
If the PSU has provided permission for ReadTransactionsCredits, the ASPSP must include all credits including debit reversals.
If the PSU has provided permission for ReadTransactionsDebits, the ASPSP must include all debits including credit reversals.
The ExpirationDateTime is an optional field which specifies the expiration for AISP access to the PSU's data.
The field is optional - as the consent for AISP access to a PSU's data may be indefinite. The ExpirationDateTime is different to the RTS requirement for a PSU to re-authorise after 90 days - which is clarified in the "RTS and SCA Exemptions" section. The same account-request resource will be re-authenticated - with the same ExpirationDateTime as the original request.
The ExpirationDateTime applies to all Permissions (data clusters) being consented.
The TransactionToDateTime and the TransactionFromDateTime specify the period for consented transaction and/or statement history. Both the fields are optional and one may be specified without the other.
The AISP must be restricted to accessing transactions within this period when accessing the transactions resource.
The AISP must be restricted to accessing statements which are completely within this period when accessing the statements resource.
The Account Request resource may have one of the following status codes after authorisation has taken place:
| Status | Description | |
|---|---|---|
| 1 | Authorised | The account request has been successfully authorised. |
| 2 | Rejected | The account request has been rejected. |
| 3 | Revoked | The account request has been revoked via the ASPSP interface. |
A PSU may revoke consent for accessing account information at any point in time.
A PSU may revoke authorisation directly with the ASPSP. The mechanisms for this are in the competitive space and are up to each ASPSP to implement in the ASPSP's banking interface. If the PSU revokes authorisation with the ASPSP, the Status of the account-request resource must be set to Revoked.
The PSU may request the AISP to revoke consent that it has authorised. If consent is revoked with the AISP:
The PSU must select the accounts to which the consent should be applied at the point of consent authorisation.
Subsequent changes to the set of accounts to which the consent authorisation applies may be carried out directly with the ASPSP. The method for doing this lies in the competitive space and is not part of this specification.
Additionally, the set of selected accounts may also change due to external factors. This includes (but is not limited to):
In such a situation, only the affected account is removed from the list of selected accounts. The ASPSP must not revoke authorisation to other accounts.
Information for risk scoring and assessment will come via:
No fields for business logic security concerns have been identified for the Account Info APIs.
For Accounts & Transaction APIs, the Meta section in API responses may contain two additional fields to indicate the date range for which data has been returned.
The transactions or statements for a particular range of dates may be excluded from the response because:
The absence of transactions / statements in the payload does not indicate that there were no transactions / statements during that period.
To ensure that the data is interpreted correctly, the ASPSP may provide the date of the first available transaction and last available transaction as part of the response in the Meta section in the FirstAvailableDateTime and LastAvailableDateTime fields.
"Meta": {
"TotalPages": 1,
"FirstAvailableDateTime": "2017-05-03T00:00:00+00:00",
"LastAvailableDateTime": "2017-12-03T00:00:00+00:00"
} |
The Account Info API resources, where possible, have been borrowed from the ISO 20022 camt.052 XML standard. However - has been adapted for APIs based as per our design principles.
Deviations from the camt.052 XML standard are:
Variations for the transactions structure include:
Renaming "entry" to "transaction" for consistency - as this is the language used in the CMA Order, and PSD2
DateTime elements used instead of a complex choice of Date and DateTime
Flattening of the structure for BankTransactionCode and ProprietaryBankTransactionCode
Additional information for an AddressLine, MerchantDetails, and a running Balance
Each of the Account and Transaction API resources are documented in sub-pages of this specification. Each resource is documented with:
The Swagger Specification for Account Information APIs can be downloaded from the following links: