Read/Write Data API Specification - v3.0
Version Control
| Version | Date | Author | Comments |
|---|---|---|---|
| 2.0-rc1 | OB R/W API Team | This is the initial draft version for rc1 | |
| 2.0-rc2 | OB R/W API Team | Moved Usage Examples from Account and Transactions Specification to this page Updated the Response Headers section to state the x-fapi-interaction-id should be generated if required. Matches FAPI specification. Clarified that x-fapi-financial-id corresponds to the organization id of the ASPSP in the Open Banking Directory. Clarified that x-jws-signature is only valid for some APIs. Removed x-jws-signature from examples. Changes to the Message Signing section to:
Added error code 415 Unsupported Media Type, for invalid Content-Type header value | |
| 2.0-rc3 | OB R/W API Team | This is the initial draft version for rc3. Updates:
Errata:
| |
| 3.0-draft1 | OB R/W API Team | No change. | |
| 3.0-draft2 | OB R/W API Team | No Change | |
| 3.0-draft3 | OB R/W API Team | Clarified that x-fapi-financial-id should be validated. Clarified wording in 400 (Bad Request) v/s 404 (Not Found) section from "If an ASPSP has not implemented an optional API, it must respond with a 404 (Not Found) for requests to that URL." to "If an ASPSP has not implemented an API endpoint, it must respond with a 404 (Not Found) for requests to that URL." | |
| 3.0-draft4 | OB R/W API Team | Clarified use of Idempotency Key. Updated Resource URI Path Structure to state the use of API pre-fixes for [resource-group] based on 132 | |
| 3.0-draft5 | OB R/W API Team | Updated examples to change UTC to GMT to be in line with https://tools.ietf.org/html/rfc7231#page-66 Clarified the usage of the http://openbanking.org.uk/iss field in the JOSE header for non-repudiation Clarified in "Return & Error Codes" that an ASPSP must return a 429 when a request has been throttled. Clarified the definition of Content-Type and Accept header behaviour. Specifically, added "The TPP may provide additional information (e.g. a 'q' value and charset). " | |
| 3.0-draft6 | OB R/W API Team | Some further tightening up on "Return & Error Codes" (429) and that it must be documented as part of fair usage policies. Modified definition for 400s to state that they could be used for DELETE and GET requests. Also stated that incorrect headers may lead to 400s. Added OAuth Error Code alignment as a must for ASPSP to implement Added Error Response Structure and Error Codes for response payload Updated Message Signing principles (out of date text removed) Clarified detail on the use of RS256/PS256 as a signing algorithm. Added Data / Enumerations to document how namespaced enumerations are used Added Date Format Guideline for ASPSPs: An ASPSP must accept all valid ISO-8601 date formats including its permitted variations (e.g. variations in how the timezone is defined, dates with or with a seconds or milliseconds part etc.) in the requests. | |
| 3.0-draft7 | OB R/W API Team | Added more ErrorCode(s) in the CodeList Removed Error Response/Codes for Http Error: 401, 403 and 429. Updated the Authorized Intent example from "AwaitingAuthorisation" to “Revoked“ state Rewrote "Changes to an Intent's Authorized State" so that it is clearer. Added a section on Data Model / Common Payload Structure / Optional Fields to ensure that optional fields are encoded consistently. | |
| 3.0-RC2 | OB R/W API Team | Re-ordered Error Code table and fixed grammatical errors. Clarified that Error Code types for UK.OBIE.Signature.* only relate to the x-jws-signature. Changed the title of Basics → Return & Error Codes to Basics / HTTP Status Codes Modified the Error Descriptions to clarify what should be populated into path and url fields Modified the UK.OBIE. Listed child pages as API specifications in Overview section. Modifications to cater to re-authentication:
Modifications for the introduction of CIBA
| |
| 3.0-RC3 | OB R/W API Team | Renamed the Refresh Token expiry field from Type of the Removed reference of Discovery API Specification from Overview section. For information note added in Supported Grant Types / CIBA on status of the CIBA profile. Consent Re-authorisation section and content within, is renamed to Consent Re-authentication (for Authorised Consents) In OBErrorResponse1 object - increased the size of:
Added Security & Access Control / Consent Authorisation / Exemptions from Strong Customer Authentication to clarify that the spec does not dwell upon this topic. Replaced section on 'Definition of Optionality' with new section on 'Categorisation of implementation requirements'. Added Updated Code definition in data dictionary. Updated Error Code Usage Example with valid code and values. updates:
| |
| 3.0 | OB R/W API Team | This is the baseline version. No change from RC3. |
Overview
The Read/Write Data API Specification provides a description of the elements that are common across all the Read/Write Data APIs.
This specification should be read in conjunction with the individual Read/Write API Specifications for:
- Account and Transaction API Specification - v3.0
- Payment Initiation API Specification - v3.0
- Confirmation of Funds API Specification - v3.0
- Event Notification API Specification - v3.0
This specification should be read in conjunction with the Customer Experience Guidelines and Management Information Requirements. Together these form the OBIE standard, which should enable any ASPSP which implements the specification to meet their obligations under both the CMA Order and PSD2/RTS.
The key difference between the CMA Order and PSD2/RTS requirements relate to which product types are implemented, and the timing for implementation. For example, the CMA Order requires the CMA9 to implement the standard for PCA and BCA accounts earlier (in some cases) than the PSD2/RTS timelines. The timings are defined in the Open Banking Roadmap (https://www.openbanking.org.uk/wp-content/uploads/Open-Banking-Revised-Roadmap-July-2018.pdf).
Document Structure
This document consists of the following parts:
Overview: Provides an overview of the scope of the API and the key decisions and principles that contributed to the specification.
Basics: The section begins with an introduction to how the APIs are used.
Security & Access Control: Specifies the means for TPPs and PSUs to authenticate themselves and provide consent.
Data Model: Describes the data model for the API payloads.
Known Issues
This document and its sub-pages must be read in conjunction with the Known Issues.
Design Principles
RESTful APIs
The API adheres to RESTful API concepts where possible and sensible to do so.
However, the priority is to have an API that is simple to understand and easy to use. In instances where following RESTful principles would be convoluted and complex, the principles have not been followed.
References:
- The highest level Data Description Language used is the JSON Schema : http://json-schema.org/
- Best Practice has also been taken from the Data Description Language for APIs; JSON API : http://jsonapi.org/
- The Interface Description Language used is the Swagger Specification version 2.0 (also known as Open API) : http://swagger.io/ and
Standards
The OBIE principles for developing API standards:
- OBIE will adopt existing standards where relevant/appropriate to minimise re-inventing the wheel.
- The Standards currently being reviewed include ISO20022, and FAPI.
- OBIE will favour developer/user experience over and above adoption of existing Standards, in order to create a more future proof Standard.
- OBIE will work with other relevant bodies to align with, contribute to and/or adopt other Standards work, especially relating to creation of Standards around APIs and JSON payloads.
ISO 20022
The CMA Order requires the CMA9 Banks to be aligned with the Regulatory and Technical Standards (RTS) under PSD2.
A previous draft of the EBA RTS required that the interface "shall use ISO 20022 elements, components or approved message definitions". In keeping with that requirement, the API payloads are designed using the ISO 20022 message elements and components where available.
The principles we have applied to re-use of ISO message elements and components are:
- Where relevant - the API payloads have been flattened so that they are more developer friendly. This has been a request from the developer community, and the stakeholders involved in the design workshop.
- Only elements that are required for the functioning of the API endpoint will be included in the API payload. API endpoints are defined for specific use-cases (not to be generically extensible for all use-cases).
- We will modify ISO 20022 elements where the existing standard does not cater for an API context (such as filtering, pagination etc.). An example is having latitude and longitude in decimal format - as this is how developers will work with latitude and longitude; or using simple types (e.g., a single date-time field) instead of a complex type (e.g., a choice field with a nesting of date and time).
Extensibility
It is intended that the API flows will be extended to cater for more complex use-cases in subsequent releases - and we have kept this in mind during the design.
Idempotency
Idempotency is difficult to implement consistently and leverage consistently.
As a result, idempotency is used sparingly in the Open Banking API specifications; with a preference to allow TPPs to simply re-submit a request under failure conditions.
APIs have been defined to be idempotent, where not doing so would cause a poor PSU user-experience or increase false positive risk indicators.
Message Signing
Digital signatures will facilitate non-repudiation for Open Banking APIs.
The approach for message signing is documented in Basics / Message Signing.
The applicability of signatures to individual requests and responses is documented on the page for each of the resources.
Agnostic to Payment Schemes
The API will be designed so that it is agnostic to the underlying payment scheme that is responsible for carrying out the payment.
As a result, we will not design field lengths and payloads to only match the Faster Payments message, and will instead rely on the field lengths and definitions in ISO 20022. Due diligence has been carried out to ensure that the API has the necessary fields to function with Bacs payments - as per agreed scope.
We will provide further mapping guidance to ensure that differences are understood between the Open Banking Payment API standard, and FPS and Bacs schemes where applicable.
Status Codes
The API uses two status codes that serve two different purposes:
- The HTTP Status Code reflects the outcome of the API call (the HTTP operation on the resource). The Security Working Group has stated that granular error codes may expose threat vectors - so these are limited to the HTTP Status Codes.
- A Status field in some of the resource payloads reflects the status of resources.
Unique Identifiers (Id Fields)
A REST resource should have a unique identifier (e.g. a primary key) that may be used to identify the resource. These unique identifiers are used to construct URLs to identify and address specific resources.
However, considering that some of the resources described in these specifications do not have a primary key in the system of record, the Id field will be optional for some resources.
An ASPSP that chooses to populate optional ID fields must ensure that the values are unique and immutable.
Categorisation of Implementation Requirements
Where a requirement is being implemented by either an ASPSP and/or a TPP, a different categorisation is applied. The functionality, endpoints and fields within each resource are categorised as 'Mandatory', 'Conditional' or 'Optional'.
ASPSPs must make documentation available to TPPs (e.g. on their developer portals) to which 'Conditional' / 'Optional' endpoints and fields are implemented for any given implementation of the specification.
Mandatory
Functionality, endpoints and fields marked as Mandatory are required in all cases for regulatory compliance and/or for the API to function and deliver essential customer outcomes.
For functionalities and endpoints:
- An ASPSP must implement an endpoint that is marked Mandatory.
- An ASPSP must implement functionality that is marked Mandatory.
For fields:
- A TPP must specify the value of a Mandatory field.
- An ASPSP must process a Mandatory field when provided by the TPP in an API request.
- An ASPSP must include meaningful values for Mandatory fields in an API response.
Conditional
Functionality, endpoints and fields marked as Conditional may be required in some cases for regulatory compliance (for example, if these are made available to the PSU in the ASPSP's existing Online Channel, or if ASPSPs (or a subset of ASPSPs) have been mandated by a regulatory requirement).
For functionalities and endpoints:
- An ASPSP must implement functionality and endpoints marked as Conditional if these are required for regulatory compliance.
For fields:
- All fields that are not marked as Mandatory are Conditional.
- A TPP may specify the value of a Conditional field.
- An ASPSP must process a Conditional field when provided by the TPP in an API request, and must respond with an error if it cannot support a particular value of a Conditional field.
- An ASPSP must include meaningful values for Conditional fields in an API response if these are required for regulatory compliance.
Optional
Functionality and endpoints marked as Optional are not necessarily required for regulatory compliance but may be implemented to enable desired customer outcomes.
For functionalities and endpoints:
- An ASPSP may implement an Optional endpoint.
- An ASPSP may implement Optional functionality.
For fields:
- There are no Optional fields.
- For any endpoints which are implemented by an ASPSP, the fields are either Mandatory or Conditional.
Basics
Actors
| Actor | Abbreviation | Type | Specializes | Description |
|---|---|---|---|---|
| Payment Service User | PSU | Person | N/A | A natural or legal person making use of a payment service as a payee, payer or both (PSD2 Article 4(10)) |
| Payment Service Provider | PSP | Legal Entity | N/A | A legal entity (and some natural persons) that provide payment services as defined by PSD2 Article 4(11) |
| Account Servicing Payment Service Provider | ASPSP | Legal Entity | PSP | An ASPSP is a PSP that provides and maintains a payment account for a payment services user (PSD 2 Article 4(15). The CMA 9 are all ASPSPs. |
| Third Party Providers / Trusted Third Parties | TPP | Legal Entity | PSP | A party other than an ASPSP that provides payment related services. The term is not actually defined in PSD2, but is generally deemed to include all payment service providers that are 3rd parties (the ASPSP and the PSU to whom the account belongs being the first two parties). References to a "TPP" in the specification relate to a piece of registered software with an ASPSP (with a specific client_id). |
| Payment Initiation Service Provider | PISP | Legal Entity | TPP | A TPP that provides Payment Initiation Services. PSD2 does not offer a formal definition. Article 4(18) quite circularly defines a PISP as a PSP that provides Payment Initiation Services. |
Account Information Service Provider | AISP | Legal Entity | TPP | A TPP that provides Account Information Services. Again, PSD2 defines AISPs in Article 4(19) circularly as a PSP that provides account information services |
| Card Based Payment Instrument Issuer | CBPII | Legal Entity | TPP | A TPP that issues card based payment instruments to PSUs and requires access to the Confirmation of Funds API. |
Character Encoding
The API requests and responses must use a UTF-8 character encoding. This is the default character encoding for JSON (RFC 7158 - Section 8.1)
However, an ASPSP's downstream system may not accept some UTF-8 characters, such as emoji characters (e.g. "Happy Birthday 🎂🎂!" may not be an acceptable Payment Reference). If the ASPSP rejects the message with a UTF-8 character that cannot be processed, the ASPSP must respond with an HTTP 400 (Bad Request) status code.
Date Formats
An ASPSP must accept all valid ISO-8601 date formats including its permitted variations (e.g. variations in how the timezone is defined, dates with or with a seconds or milliseconds part etc.) in the requests.
All dates in the JSON payloads are represented in ISO 8601 date-time format. All date-time fields in responses must include the timezone. For Example:
2017-04-05T10:43:07+00:00 2018-07-03T14:43:41Z
All dates in the query string are represented in ISO 8601 date-time format and must not include the timezone. For example:
2017-04-05T10:43:07 2017-04-05
All dates in the HTTP headers are represented as RFC 7231 Full Dates. An example is below:
Sun, 10 Sep 2017 19:43:31 GMT
All dates in the JWT claims are expressed as a JSON number representing the number of seconds from 1970-01-01T0:0:0Z as measured in GMT until the date/time.
//Sun, 12 Feb 2018 14:45:00 GMT 1518446700
Resource URI Path Structure
The path of the URI must follow the following structure (from the OB API Release Management document).
- [participant-path-prefix]/open-banking/[version]/[resource-group]/[resource]/[sub-resource]/[resource-id]
This consists of the following elements:
- [participant-path-prefix]
An optional ASPSP specific path prefix. - open-banking
The constant string "open-banking". - [version]
The version of the APIs expressed as /v[major-version].[minor-version]/. - [resource-group]
The resource-group identifies the group of endpoints, according to the PSD2 role used to access the API (as "aisp", "pisp" or "cbpii"). - [resource]/[sub-resource]/[resource-id]
Details the resource.
Examples:
/superbank/open-banking/v1.0/pisp/payments
/open-banking/v2.0/aisp/account-access-consents
/apis/open-banking/v2.1/aisp/accounts
/open-banking/v3.0/cbpii/funds-confirmation-consents
For brevity, the APIs are referred to by their resource names in these documents and in all examples.
Headers
Request Headers
| Header Value | Notes | POST Requests | GET Requests | DELETE Requests |
|---|---|---|---|---|
| x-fapi-financial-id | The unique id of the ASPSP to which the request is issued. The unique id will be issued by OB and corresponds to the Organization Id of the ASPSP in the Open Banking Directory. If the value does not match the expected value (based on the Client ID or network certificate of the caller, the ASPSP must reject the request with a 403 (Not Authorized) status code. | Mandatory | Mandatory | Mandatory |
| x-fapi-customer-last-logged-time | The time when the PSU last logged in with the TPP. | Optional | Optional | Optional |
| x-fapi-customer-ip-address | The PSU's IP address if the PSU is currently logged in with the TPP. | Optional | Optional | Optional |
| x-fapi-interaction-id | An RFC4122 UID used as a correlation id. If provided, the ASPSP must "play back" this value in the x-fapi-interaction-id response header. | Optional | Optional | Optional |
| Authorization | Standard HTTP Header; Allows Credentials to be provided to the Authorisation / Resource Server depending on the type of resource being requested. For OAuth 2.0 / OIDC, this comprises of either the Basic / Bearer Authentication Schemes. | Mandatory | Mandatory | Mandatory |
| Content-Type | Standard HTTP Header; Represents the format of the payload being provided in the request. This must be set to application/json. The TPP may provide additional information (e.g. a 'q' value and charset). If set to any other value, ASPSP must respond with a 415 Unsupported Media Type. | Mandatory | Do not use | Do not use |
| Accept | Standard HTTP Header; Determine the Content-Type that is required from the Server. If specified, it must indicate that the only a JSON response is accepted (e.g by setting the value to For endpoints that do not respond with JSON (e.g GET ../statements/{StatementId}/file), the ASPSP must specify the available options on their developer portals. The TPP may provide additional information (e.g. a 'q' value and charset). If set to an unacceptable value the ASPSP must respond with a 406 Not Acceptable. If not specified, default is application/json | Optional | Optional | Do not use |
| x-idempotency-key | Custom HTTP Header; Unique request identifier to support idempotency. Mandatory for POST requests to idempotent resource end-points. Must not be specified for other requests. | Optional | Do not use | Do not use |
| x-jws-signature | Header containing a detached JWS signature of the body of the payload. Refer to resource specific documentation on when this header must be specified. | API specific | API specific | API specific |
x-customer-user-agent | The header indicates the user-agent that the PSU is using. The TPP may populate this field with the user-agent indicated by the PSU. If the PSU is using a TPP mobile app, the TPP must ensure that the user-agent string is different from browser based user-agent strings. | Optional | Optional | Optional |
(Reference: Section 6.3 - Financial API — Part 1: Read Only API Security Profile (Implementer’s Draft).)
Whether the PSU is present or not-present is identified via the x-fapi-customer-ip-address header. If the PSU IP address is supplied, it is inferred that the PSU is present during the interaction.
The implications to this are:
- ASPSPs will need to rely on AISPs assertion.
- As agreed at TDA (18/05), it will be up to the ASPSPs to interpret the 4-times customer not present rule - to be within the “spirit” of the RTS requirement.
- This is dependent on GDPR considerations on the AISP passing a PSU's IP address to an ASPSP.
Response Headers
| Header Value | Notes | Mandatory? |
|---|---|---|
| Content-Type | Standard HTTP Header; Represents the format of the payload returned in the response. The ASPSP must return Content-Type: application/json as a content header for all endpoints, except the GET ../statements/{StatementId}/file endpoint, where it is up to the ASPSP to specify available options. | Mandatory |
| x-jws-signature | Header containing a detached JWS signature of the body of the payload. Refer to resource specific documentation on when this header must be returned. | API specific |
| x-fapi-interaction-id | An RFC4122 UID used as a correlation id. The ASPSP must set the response header | Mandatory |
| Retry-After | Header indicating the time (in seconds) that the TPP should wait before retrying an operation. The ASPSP should include this header along with responses with the HTTP status code of 429 (Too many requests). | Optional |
HTTP Status Codes
The following are the HTTP response codes for the different HTTP methods - across all Read/Write API endpoints.
Situation | HTTP Status | Notes | Returned by POST | Returned by GET | Returned by DELETE |
|---|---|---|---|---|---|
| Query completed successfully | 200 OK | No | Yes | No | |
| Normal execution. The request has succeeded. | 201 Created | The operation results in the creation of a new resource. | Yes | No | No |
| Delete operation completed successfully | 204 No Content | No | No | Yes | |
Request has malformed, missing or non-compliant JSON body, URL parameters or header fields. | 400 Bad Request | The requested operation will not be carried out. | Yes | Yes | Yes |
Authorization header missing or invalid token | 401 Unauthorized | The operation was refused access. Re-authenticating the PSU may result in an appropriate token that may be used. | Yes | Yes | Yes |
Token has incorrect scope or a security policy was violated. | 403 Forbidden | The operation was refused access. Re-authenticating the PSU is unlikely to remediate the situation. | Yes | Yes | Yes |
| The TPP tried to access the resource with a method that is not supported. | 405 Method Not Allowed | Yes | Yes | Yes | |
| The request contained an Accept header other than permitted media types and a character set other than UTF-8 | 406 Not Acceptable | Yes | Yes | Yes | |
| The operation was refused because the payload is in a format not supported by this method on the target resource. | 415 Unsupported Media Type | Yes | No | No | |
| The operation was refused as too many requests have been made within a certain timeframe. | 429 Too Many Requests | ASPSPs may throttle requests when they are made in excess of their fair usage policy. ASPSPs must document their fair usage policies in their developer portals. The ASPSP must respond with this status if it throttles the request. The ASPSP should include a Retry-After header in the response indicating how long the TPP must wait before retrying the operation. | Yes | Yes | Yes |
| Something went wrong on the API gateway or micro-service | 500 Internal Server Error | The operation failed. | Yes | Yes | Yes |
An ASPSP MAY return other standard HTTP status codes (e.g. from gateways and other edge devices) as described in RFC 7231 - Section 6.
ASPSPs must respond with error response in the OAuth/OIDC flow with mandatory alignment of error codes to those specified in RFC 6749 Section 4.1.2.1
ASPSPs must respond with Open Banking Error Response Structure for all errors during API Calls.
400 (Bad Request) v/s 404 (Not Found)
When a TPP tries to request a resource URL with a resource Id that does not exist, the ASPSP must respond with a 400 (Bad Request) rather than a 404 (Not Found).
e.g., if a TPP tries to GET /domestic-payments/22289 where 22289 is not a valid DomesticPaymentId, the ASPSP must respond with a 400.
When a TPP tries to request a resource URL that results in no business data being returned (e.g. a request to retrieve standing order on an account that does not have standing orders) the ASPSP must respond with a 200 (OK) and set the array to be empty.
If the TPP tries to access a URL for a resource that is not defined by these specifications (e.g. GET /card-accounts), the ASPSP may choose to respond with a 404 (Not Found).
If an ASPSP has not implemented an API endpoint, it must respond with a 404 (Not Found) for requests to that URL.
The table below illustrates some examples of expected behaviour:
| Situation | Request | Response |
|---|---|---|
| TPP attempts to retrieve a payment with a DomesticPaymentId that does not exist | GET /domestic-payments/1001 | 400 (Bad Request) |
| TPP attempts to retrieve a resource that is not defined | GET /bulk | 404 (Not Found) |
TPP attempts to retrieve a resource that is in the specification, but not implemented by the ASPSP. e.g., an ASPSP has chosen not to implement the status API endpoint for domestic-scheduled-payments | GET /domestic-scheduled-payments/1002 | 404 (Not Found) |
| TPP attempts to retrieve standing orders for an AccountId that exists, but does not have any standing orders | GET /accounts/1000/standing-orders | 200 OK {
"Data": {
"StandingOrder": []
},
"Links": {
"Self": "https://api.alphabank.com/open-banking/v1.0/accounts/1000/standing-orders/"
},
"Meta": {
"TotalPages": 1
}
} |
403 (Forbidden)
When a TPP tries to access a resource that it does not have permission to access, the ASPSP must return a 403 (Forbidden).
The situation could arise when:
- The TPP uses an access token that does not have the appropriate scope to access the requested resource.
- The TPP attempted to access a resource with an Id that it does not have access to. e.g., an attempt to access GET /domestic-payments/1001 where a payment resource with id 1001 belongs to another TPP.
- The TPP tries to access an account/transaction resource, the TPP does not have a consent authorisation with the right Permissions to access the requested resource. e.g., an attempt to access GET /standing-orders when the ReadStandingOrdersBasic permission was not included in the consent authorisation.
- The TPP tries to access an account/transaction resource and the TPP does not have a consent authorisation for the AccountId. e.g., an attempt to access GET /accounts/2001 or GET /accounts/2001/transactions when the PSU has not selected AccountId 2001 for authorisation.
When the TPP uses an access token that is no longer valid, the situation could potentially be remedied by asking the PSU to re-authenticate. This should be indicated by a 401 (Unauthorized) status code.
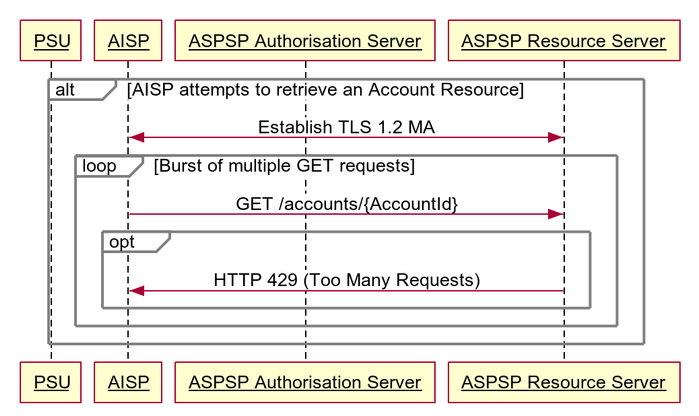
429 (Too Many Requests)
When a TPP tries to access a resource too frequently the ASPSP may return a 429 (Too Many Requests). This is a Non Functional Requirement and is down to individual ASPSPs to decide throttling limits.
This situation could arise when:
- A TPP decides to implement "Real Time Payment Status" functionality for its users and implements this badly by polling a GET endpoint or an Idempotent POST endpoint in excess of the ASPSP's fair usage policy to provide pseudo "real-time" Status updates to the user.
- A TPP decides to use the Single Immediate Payment endpoint as if it were a batch payment facility and sends a large number of payment requests in a very short space of time such that it exceeds the ASPSP's fair usage policy.
Pre-Conditions
The following pre-conditions must be satisfied in order to use these APIs:
Pre-conditions for TPPs
- The TPP must have completed onboarding on the Open Banking Directory.
- The TPP must have registered one or more software statements with the Open Banking Directory.
- To use the Payment Initiation APIs, the the software statement must have "payments" as one of the permitted scopes.
- To use the Account/Transaction APIs, the software statement must have "accounts" as one of the permitted scopes.
- To use the Confirmation of Funds APIs, the software statement must have "fundsconfirmations" as one of the permitted scopes.
- The TPP must have valid network and signing certificates issued by Open Banking.
- The TPP must have completed registration with each of the ASPSPs that it wants to transact with and have been issued with a client-id.
Pre-conditions for ASPSPs
- The ASPSP must have completed onboarding on the Open Banking Directory.
- The ASPSP must have valid network and signing certificates issued by Open Banking.
Idempotency
An idempotency key is used to guard against the creation of duplicate resources when using the POST API endpoints (where indicated).
If an idempotency key is required for an API endpoint:
- The x-idempotency-key provided in the header must be at most 40 characters in size. If a larger x-idempotency-key length is provided, the ASPSP must reject the request with a status code is 400 (Bad Request).
- The TPP must not change the request body while using the same x-idempotency-key. If the TPP changes the request body, the ASPSP must not modify the end resource. The ASPSP may treat this as a fraudulent action.
- The ASPSP must treat a request as idempotent if it had received the first request with the same x-idempotency-key from the same TPP in the preceding 24 hours.
- The ASPSP must not create a new resource for a POST request if it is determined to be an idempotent request.
- The ASPSP must respond to the request with the current status of the resource (or a status which is at least as current as what's available on existing online channels) and a HTTP status code of 201 (Created).
- The TPP must not use the idempotent behaviour to poll the status of resources.
- The ASPSP may use the message signature, along with the x-idempotency-key to ensure that the request body has not changed.
If an idempotency key is not required for an API endpoint:
- The ASPSP must ignore the idempotency key if provided.
Message Signing
Overview
This section provides an overview of how message signing is implemented for the Open Banking Read/Write APIs.
The APIs require TLS 1.2 Mutual Authentication and this may be used as a means of non-repudiation. However, it would be difficult to maintain digital records and evidence of non-repudiation if the API only relied on TLS 1.2.
A solution for non-repudiation that does not rely on TLS, would be achieved by providing a JWS with detached content (as defined in RFC 7515 - Appendix F) in the HTTP header of each API request.
The HTTP body would form an un-encoded payload as defined in RFC 7797.
The JWS would be signed using an algorithm that supports asymmetric keys.
A request would be signed by a TPP's private key and a response would be signed by the ASPSP's private key.
OB Directory will provide and host the necessary certificates containing the corresponding public keys so that the signature may be verified.
Not all API requests and responses are signed. Whether message signing is mandatory, supported or not supported is documented along with each API.
Specification
The TPP must sign the HTTP body of each API request that requires message signing.
The ASPSP must sign the HTTP body of each API response that requires message signing.
The ASPSP should verify the signature of API requests that it receives before carrying out the request. If the signature fails validation, the ASPSP must respond with a 400 (Bad Request).
The ASPSP must reject any API requests that should be signed but do not contain a signature in the HTTP header with a 400 (Bad Request) error.
The TPP should verify the signature of API responses that it receives.
The signer must sign the message with PS256.
Process for Signing a Payload
Step 1: Identify the Private Key and Corresponding Signing Certificate to be Used for Signing
The signer must use a private key that has a corresponding digital certificate (that contains the corresponding public key) issued by OB.
The signing certificate must be valid at the time of creating the JWS.
Step 2: Form the JOSE Header
The JOSE header for the signature must contain the following fields
Claim | Description |
|---|---|
alg | The algorithm that will be used for signing the JWS. The list of valid algorithms is here https://tools.ietf.org/html/rfc7518#section-3.1. At the time of publication, PS256 and ES256 are not supported and this value must be RS256. Once there is sufficient market adoption of PS256, the signing algorithm will cut over to PS256 and the use of RS256 will be deprecated. |
| typ | This is an optional claim. If it is specified, it must be set to the value "JOSE" |
| cty | This is an optional claim. If it is specified, it must be set to the value "json" or "application/json". |
kid | This must match the certificate id of the certificate selected in step 1. |
| b64 | This must have the boolean value false. This indicates that the message payload is not base64 url encoded. |
| http://openbanking.org.uk/iat | This must be a JSON number representing the number of seconds from 1970-01-01T0:0:0Z as measured in GMT until the date/time. This is a private header parameter name. (See RFC 7515 - Private Header Parameter Names) |
| http://openbanking.org.uk/iss | This must be a string that identifies the PSP. This must match the subject of the signing certificate. The OB signing certificate Subject consists of
The allows the verifier to uniquely identify the PSP and the software statement. This is a private header parameter name. (See RFC 7515 - Private Header Parameter Names) |
| crit | This must be a string array consisting of the values "b64", "http://openbanking.org.uk/iat", "http://openbanking.org.uk/iss" This indicates that the JWS signature validator must understand and process the three additional claims. |
Step 3: Compute the JWS
The signer must compute the signature as a detached JWS as defined in RFC 7515, Appendix F
"One way to do this is to create a JWS in the normal fashion using a representation of the content as the payload but then delete the payload representation from the JWS and send this modified object to the recipient rather than the JWS."
...Note that this method needs no support from JWS libraries, as applications can use this method by modifying the inputs and outputs of standard JWS libraries.
Step 4: Add the JWS as a HTTP Header
The signer must include an HTTP header called x-jws-signature with its value set to the signature computed in Step 3.
x-jws-signature: V2hhdCBoYXRoIGdvZCB3cm91Z2h0ID8=..QnkgR2VvcmdlLCBzaGUncyBnb3QgaXQhIEJ5IEdlb3JnZSBzaGUncyBnb3QgaXQhIE5vdyBvbmNlIGFnYWluLCB3aGVyZSBkb2VzIGl0IHJhaW4/
Process for Verifying a Signature
Step 1: Extract the components from the JWS
The verifier must extract and decode the JOSE header and signature from the JWS provided in the x-jws-signature.
Step 1: Validate the JOSE Header and Certificate
The verifier must validate the JOSE header to ensure that it is a valid json object with only the claims specified in Process for Signing a Payload - Step 2.
The verifier must validate that the typ header if specified has the value JOSE.
The verifier must validate that the cty header if specified it resolves to application/json.
The verifier must ensure that the specified alg is one of the algorithms specified by OB.
The verifier must ensure that the specified kid is valid and a signing certificate with the specified key id can be retrieved from the OB directory.
The verifier must ensure that the b64 claim is set to false.
The verifier must ensure that the http://openbanking.org.uk/iat claim has a date-time value set in the past.
The verifier must ensure that the http://openbanking.org.uk/iss claim matches the dn of the certificate.
The verifier must ensure that the crit claim does not contain additional critical elements.
Step 3: Verify the Signature
The verifier must verify the signature as defined in RFC 7515, Appendix F.
To use the modified object, the recipient reconstructs the JWS by re-inserting the payload representation into the modified object and uses the resulting JWS in the usual manner. Note that this method needs no support from JWS libraries, as applications can use this method by modifying the inputs and outputs of standard JWS libraries.
Sample JOSE Header
{
"alg": "RS512",
"kid": "90210ABAD",
"b64": false,
"http://openbanking.org.uk/iat": 1501497671,
"http://openbanking.org.uk/iss": "C=UK, ST=England, L=London, O=Acme Ltd.",
"crit": [ "b64", "http://openbanking.org.uk/iat", "http://openbanking.org.uk/iss"]
}
Filtering
An ASPSP must provide limited support of filtering on GET operations that return multiple records.
The filter parameters, are always specific to particular field(s) of the resource, and follow the rules/formats defined under the resource's data dictionary.
In case of DateTime type filter parameters, values must be specified in ISO8601 format. If the DateTime contains a timezone, the ASPSP must ignore the timezone component.
The filter values will be assumed to refer to the same timezone as the timezone in which the resource is maintained.
Pagination
An ASPSP MAY provide a paginated response for GET operations that return multiple records.
In such a situation, the ASPSP MUST:
- If a subsequent page of resource records exists, the ASPSP must provide a link to the next page of resources in the Links.Next field of the response. The absence of a next link would indicate that the current page is the last page of results.
- If a previous page of resource records exists, the ASPSP must provide a link to the previous page of resources in the Links.Prev field of the response. The absence of a prev link would indicate that the current page is the first page of results.
For a paginated responses, the ASPSP SHOULD ensure that the number of records on a page are within reasonable limits - a minimum of 25 records (except on the last page where there are no further records) and a maximum of 1000 records.
Additionally, the ASPSP MAY provide:
- A link to the first page of results in the Links.First field.
- A link to the last page of results in the Links.Last field.
- The total number of pages in the Meta.TotalPages field.
As with all other responses, the ASPSP MUST include a "self" link to the resource in the Links.Self field as described in the Links sections.
This standard does not specify how the pagination parameters are passed by the ASPSP and each ASPSP may employ their own mechanisms to paginate the response.
If the original request from the AISP included filter parameters, the paginated response must return only results that match the filter.
ASPSPs are not expected to implement pagination with transaction isolation. The underlying data-set may change between two subsequent requests. This may result in situations where the same transaction is returned on more than one page.
Archiving
Archiving of resources will be for ASPSPs to defined based on their internal Legal and Regulatory requirements.
In addition:
ASPSPs must only delete expired intent-ids 24 hours after creation
- ASPSPs may archive these expired intent-ids
Security & Access Control
Scopes & Grant Types
To access each of the APIs, the API must be called with an access token in the HTTP Authorization header.
The scopes required with these access tokens and the grant type used to get the access token are specified in the specific API documentation.
Consent Authorisation
OAuth 2.0 scopes are coarse grained and the set of available scopes are defined at the point of client registration. There is no standard method for specifying and enforcing fine grained scopes (e.g. a scope to enforce payments of a specified amount on a specified date).
An intent is used to define the fine-grained permissions that are granted by the PSU to the TPP.
The act of providing authorisation of an intent by a PSU to an ASPSP is called consent authorisation.
The Open Banking Read/Write APIs use a variety of intents such payments and account-requests.
A TPP requests an ASPSP to create intent by using a client credentials grant. The ASPSP creates the intent and responds with the intent-id. The TPP then redirects the PSU to the ASPSP to authorise consent for the intent, passing in an intent-id as a parameter.
This is done through an authorization grant flow and results in the issuance of an access token tied to the authorised intent.
An access token is bound to a single PSU and an intent.
Error Condition
If the PSU does not complete a successful consent authorisation (e.g. if the PSU is not authenticated successfully), the authorization code grant ends with a redirection to the TPP with an error response as described in RFC 6749 Section 4.1.2.1. The PSU is redirected to the TPP with an error parameter indicating the error that occurred.
Token Expiry Time
The expiry time for issued access tokens and refresh tokens must be deterministic for the TPP.
In order to achieve this:
- The ASPSP must indicate the lifetime in seconds of the access token in the
expires_infield of the JSON object returned by the token end-point. (See https://tools.ietf.org/html/rfc6749#section-4.2.2) - If the ASPSP issues a refresh token, the ASPSP must indicate the date-time at which the refresh token will expire in a claim named
http://openbanking.org.uk/refresh_token_expires_atin the id token (returned by the token end-point or userinfo end-point). Its value MUST be a number containing a NumericDate value, as specified in https://tools.ietf.org/html/rfc7519#section-2 - NumericDate is a JSON numeric value representing the number of seconds from 1970-01-01T00:00:00Z UTC until the specified UTC date-time, ignoring leap seconds.
- If the ASPSP does not issue a refresh token, the ASPSP must not populate the
http://openbanking.org.uk/refresh_token_expires_atclaim in the id token - If the ASPSP issues a refresh token that does not expire, the ASPSP must populate the claim named
http://openbanking.org.uk/refresh_token_expires_atin the id token with a value representing the number of seconds to 03:14:07 UTC on 19 January 2038 (end of UNIX epoch)
Exemptions from Strong Customer Authentication
The PSD2 RTS specifies the conditions under which a payment services provider is exempt from carrying out strong customer authentication.
This specification does not provide any direction or guidance on the application of these exemptions.
Supported Grant Types
OAuth2.0 and OIDC provide support for a variety of methods for the Authorization Server to issue an access token to the Client. These methods are called Grants.
Some of these Grant Types only identify the client, but not the resource owner. It is sufficient to provide the client's identity.
On the other hand, other grant types identify the client and resource owner. The resource owner must be authenticated to issuue access tokens through such a grant type.
The Open Banking Read/Write specification supports a sub-set of these grants as well as the FAPI Profile CIBA grant.
The security profile describes these grants in detail.
Grant Types for identifying the TPP
Client Credentials Grant
Some of the APIs can be accessed using an access token issued through a Client Credentials Grant. These APIs do not execute in the context of a consent or of a PSU and it is sufficient to identify and authenticate the TPP in order to call these APIs.
The Client Credentials Grant is documented in Section 4.4 of the OAuth 2.0 RFC
Grant Types for identifying the TPP and PSU
Authorization Code Grant & Hybrid Grant
APIs that require the PSU as well as TPP to be identified and authenticated can only be accessed using an access token issued through an Authorization Code Grant, Hybrid Grant or CIBA.
The Authorization Code Grant (see Section 4.1 of the OAuth 2.0 RFC and Section 3.1 of the OIDC Specification) can be used to redirect a PSU to the ASPSP's authorization pages in order to authenticate the PSU and generate and authorization code. The TPP can then exchange this authorization code for an access token by calling the ASPSP's token end-point and authenticating itself.
The Hybrid Grant (See Section 3.3. of the OIDC Specification) provides another redirect based mechanism for authenticating PSUs that is deemed to be more secure than using the Authorization Code Grant.
The Open Banking Security Profile - Implementators Draft 1.1.2, The UK Open Banking Security Profile and FAPI read & Write API Security Profile specify a more stringent set of requirements that ASPSPs and TPPs must adhere to.
CIBA
An ASPSP may optionally implement the CIBA flow to allow PSUs to authenticate themselves using a decoupled authentication device that is distinct from the consumption device on which they consume the TPP application.
The Client Initiated Back-channel Authentication flow is part of the MODRNA specifications. A FAPI Profile of the CIBA specification is available and ASPSPs that implement CIBA must adhere to the profile.
Identifying the PSU
ASPSPs that implement CIBA must support one or more of the following methods of identifying the PSU that is to be authenticated (either via the - login_hint_token or id_token_hint):
- User ID: Using a static identifier that is shared by the ASPSP and the PSU. This could include a static identifier issued by the ASPSP (e.g., a user name, card number, account number) or a public identifier that allows the ASPSP to uniquely identify the PSU (e.g., an email address or phone number)
- Ephemeral User ID: Using a dynamically generated, single use identifier issued by the ASPSP to the PSU. This could be a single use token generated on the PSU's authentication device or communicated to the PSU by any other means.
- Intent ID: Using an intent id generated from a POST to a consent resource with the ASPSP (e.g., a POST to /domestic-payment-consents results in a ConsentId being generated) The ASPSP then uses this information to bind the consent to a particular PSU.
- ID Token: Using a previously issued id_token that identifies the PSU. The ASPSP may limit the use of the id_token to the TPP to which it was issued.
An ASPSP must document on their developer portal, the methods of identifying a PSU the ASPSP supports.
If the ASPSP does not support a specific method of identifying a PSU, the ASPSP must return an authentication error with the error field set to invalid_request.
Identifying the PSU Using a User ID
To identify a PSU through a user id, the TPP must issue login_hint_token in the bc_authorize request that contains:
- The custom claim
http://openbanking.org.uk/sitset to the valueUID - At least one of the following claims with a value indiciating the user id:
- sub
- preferred_username
- phone_number
If the ASPSP support identification of the user through a static identifier, it must document on its developer portal the claims that it supports as a static identifier.
Identifying the PSU Using an Ephemeral User Id
To identify a PSU through an ephemeral user id, the TPP must issue a login_hint_token in the bc_authorize request that contains:
- The custom claim
http://openbanking.org.uk/sitset to the valueEUID - The claim
subpopulated with the ephemeral user id
Identifying the PSU Using an Intent ID
To identify a PSU through an intent ID, the TPP must first create a consent resource with the ASPSP.
The PSU must then issue a login_hint_token in the bc_authorize request that contains:
- The custom claim
http://openbanking.org.uk/sitset to the value IID - The claim
http://openbanking.org.uk/openbanking_intent_idset to the value of the intent id that is being used.
Identifying the PSU Using a Previously Issued Id Token
To identify a PSU through a previously isued id_token the TPP must issue an id_token_hint containing the id_token in the bc_authorize request.
Changes to an Intent's Authorized State
A PSU may revoke their consent either through the TPP or directly through the ASPSP. This only applies to long-lived consents.
- When a PSU does not complete the consent-authorisation flow, the ASPSP must mark the consent as
Rejected. - When the PSU revokes their consent with the ASPSP, the ASPSP must mark the underlying intent status as
Revoked. - When the PSU revokes their consent with the TPP, the TPP must make a
DELETErequest to the consent resource. The ASPSP must delete the resource (possibly as a "soft" delete) and respond to subsequent GET requests with an Http Status of 400.
In each of the above cases, the consent states are terminal ie the ASPSP must not allow any further state changes. The ASPSP must not permit any authorisation code grants to be initiated with such a consent.
Effect of Token Expiry on an Intent's Authorized State
An ASPSP may issue an access token and refresh token for a long-lived consent. These tokens may expire before the consent expires. In such a situation, the state of the intent does not change and the ASPSP must not modify the state of the intent.
Consent Re-authentication
Ability to re-authenticate an Authorised consent at any point of time
A TPP may request a PSU to re-authenticate a consent at any point of time for a long-lived consent that is in the Authorised state. This includes before and after the underlying tokens have expired.
An ASPSP must accept a request from a TPP to re-authenticate a consent at any point of time for a long-lived consent that is in the Authorised state. This includes before and after the underlying tokens have expired.
Once a consent re-authentication is successful, the TPP must not use access tokens and refresh tokens that were previously issued for the same consent.
When an ASPSP issues a new access token and refresh token as a result of consent re-authentication, it may invalidate the previously issued access tokens and refresh tokens for the same consent.
Low Friction User Experience
A PSU's consent re-authentication user experience must be aligned with the low friction user experience defined in the guidelines.
Use of Refresh Token
An ASPSP may issue a refresh token along with an access token as a result of consent re-authentication.
When an access token expires, the TPP may attempt to get a new access and refresh token as defined in Section 6 of the OAuth 2.0 specification.
Data Model
Common Payload Structure
This section gives an overview of the top level structure for the API payloads for the Open Banking Read/Write APIs.
The data contained within the Data section is documented with each individual API endpoint.
Request Structure
The top level request structure for Open Banking Read/Write APIs:
{
"Data": {
...
},
"Risk": {
...
}
}
Data
The Data section contains the request data for the specific API request.
The structure of this element differs for each API endpoint.
Risk
The Risk section contains risk indicators for the specific API request as provided by the TPP.
The risk indicators contained in this element may be different for each API endpoint.
Response Structure
The top level response structure for Open Banking Read/Write APIs:
{
"Data": {
...
},
"Risk": {
...
},
"Links": {
...
},
"Meta": {
...
}
}
In line with the principle of RESTful APIs, the full resource must be replayed as part of the response.
Two additional top-level sections are included in the response for:
Links
Meta
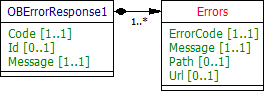
Error Response Structure
The error response structure for Open Banking Read/Write APIs:
{
"Code": "...",
"Id": "...",
"Message": "...",
"Errors": [
{
"ErrorCode": "...",
"Message": "...",
"Path": "...",
"Url": "..."
}
]
}
UML Diagram
Data Dictionary
Name | Occurrence | XPath | EnhancedDefinition | Class | Codes | Pattern |
|---|---|---|---|---|---|---|
| OBErrorResponse1 | OBErrorResponse1 | An array of detail error codes, and messages, and URLs to documentation to help remediation. | OBErrorResponse1 | |||
| Code | 1..1 | OBErrorResponse1/Code | High level textual error code, to help categorize the errors. | Max40Text | ||
| Id | 0..1 | OBErrorResponse1/Id | A unique reference for the error instance, for audit purposes, in case of unknown/unclassified errors. | Max40Text | ||
| Message | 1..1 | OBErrorResponse1/Message | Brief Error message, e.g., 'There is something wrong with the request parameters provided' | Max500Text | ||
| Errors | 1..n | OBErrorResponse1/Errors | OBError1 | |||
| ErrorCode | 1..1 | OBErrorResponse1/Errors/ErrorCode | Low level textual error code, e.g., UK.OBIE.Field.Missing | Max128Text | ||
| Message | 1..1 | OBErrorResponse1/Errors/Message | A description of the error that occurred. e.g., 'A mandatory field isn't supplied' or 'RequestedExecutionDateTime must be in future' OBIE doesn't standardise this field | Max500Text | ||
| Path | 0..1 | OBErrorResponse1/Errors/Path | Recommended but optional reference to the JSON Path of the field with error, e.g., Data.Initiation.InstructedAmount.Currency | Max500Text | ||
| Url | 0..1 | OBErrorResponse1/Errors/Url | URL to help remediate the problem, or provide more information, or to API Reference, or help etc | xs:anyURI |
Standard Error Code(s)
| HTTP Status Category | Code | Description |
|---|---|---|
| 400 | UK.OBIE.Field.Expected | For the scenario, when a field-value is not provided in the payload, that is expected in combination with preceding field-value pairs. The corresponding e.g. |
| 400 | UK.OBIE.Field.Invalid | An invalid value is supplied in one of the fields. Reference of the invalid field should be provided in the path field, and url field may have the link to a website explaining the valid behaviour. The error message should describe the problem in detail. |
| 400 | UK.OBIE.Field.InvalidDate | An invalid date is supplied, e.g., When a future date is expected, a date in past or current date is supplied. The message can specify the actual problem with the date. The reference of the invalid field should be provided in the path field, and URL field may have the link to a website explaining the valid behaviour |
| 400 | UK.OBIE.Field.Missing | A mandatory field, required for the API, is missing from the payload. This error code can be used, if it is not already captured under the validation for UK.OBIE.Resource.InvalidFormat. Reference of the missing field should be provided in the path field, and URL field may have the link to a website explaining the valid behaviour |
| 400 | UK.OBIE.Field.Unexpected | For the scenario, when a field-value is provided in the payload, that is not expected in combination with preceding field-value pairs. E.g. ContractIdentification must not be specified with [Actual/Indicative] RateType. ContractIdentification should be specified in the path element ExchangeRate must not be specified with [Actual/Indicative] RateType. ExchangeRate should be specified in the path element. InstructionPriority must not be specified with LocalInstrument. InstructionPriority should be specified in the path element. |
| 400 | UK.OBIE.Header.Invalid | An invalid value is supplied in the HTTP header. HTTP Header should be specified in the path element. |
| 400 | UK.OBIE.Header.Missing | A required HTTP header has not been provided. HTTP Header should be specified in the path element. |
| 400 | UK.OBIE.Resource.ConsentMismatch | {payment-order-consent} and {payment-order} resource mismatch. For example, if an element in the resource’s Initiation or Risk section does not match the consent section. The path element should be populated with the field of the resource that does not match the consent. |
| 400 | UK.OBIE.Resource.InvalidConsentStatus | The resource’s associated consent is not in a status that would allow the resource to be created. E.g., if a consent resource had a status of AwaitingAuthorisation or Rejected, a resource could not be created against this consent. The path element should be populated with the field in the consent resource that is invalid. |
| 400 | UK.OBIE.Resource.InvalidFormat | When the Payload schema doesn't match to the endpoint, e.g., /domestic-payments endpoint is called with a JSON Payload, which cannot be parsed into a class OBWriteDomestic1 |
| 400 | UK.OBIE.Resource.NotFound | Returned when a resource with the specified id does not exist (and hence could not be operated upon). |
| 400 | UK.OBIE.Rules.AfterCutOffDateTime | {payment-order} consent / resource received after CutOffDateTime |
| 400 | UK.OBIE.Signature.Invalid | The signature header x-jws-signature was parsed and has a valid JOSE header that complies with the specification. However, the signature itself could not be verified. |
| 400 | UK.OBIE.Signature.InvalidClaim | The JOSE header in the x-jws-signature has one or more claims with an invalid value. (e.g. a kid that does not resolve to a valid certificate). The name of the missing claim should be specified in the path field of the error response. |
| 400 | UK.OBIE.Signature.MissingClaim | The JOSE header in the x-jws-signature has one or more mandatory claim(s) that are not specified. The name of the missing claim(s) should be specified in the path field of the error response. |
| 400 | UK.OBIE.Signature.Malformed | The x-jws-signature in the request header was malformed and could not be parsed as a valid JWS. |
| 400 | UK.OBIE.Signature.Missing | The API request expected an x-jws-signature in the header, but it was missing. |
| 400 | UK.OBIE.Signature.Unexpected | The API request was not expecting to receive an x-jws-signature in the header, but the TPP made a request that included an x-jws-signature. |
| 400 | UK.OBIE.Unsupported.AccountIdentifier | The account identifier is unsupported for the given scheme. The path element should be populated with the path of the AccountIdentifier. |
| 400 | UK.OBIE.Unsupported.AccountSecondaryIdentifier | The account secondary identifier is unsupported for the given scheme. The path element should be populated with the path of the AccountSecondaryIdentifier. |
| 400 | UK.OBIE.Unsupported.Currency | The currency is not supported. Use UK.OBIE.Field.Invalid for invalid Currency. The path element should be populated with the path of the Currency. The URL should be populated with a link to ASPSP documentation listing out the supported currencies. |
| 400 | UK.OBIE.Unsupported.Frequency | Frequency is not supported. The path element should be populated with the path of the Frequency. The URL should be populated with a link to ASPSP documentation listing out the supported frequencies. |
| 400 | UK.OBIE.Unsupported.LocalInstrument | LocalInstrument is not supported by the ASPSP. The path element should be populated with the path of the LocalInstrument. The URL should be populated with a link to ASPSP documentation listing out the supported local instruments. |
| 400 | UK.OBIE.Unsupported.Scheme | Identification scheme is not supported. The path element should be populated with the path of the scheme. The URL should be populated with a link to ASPSP documentation listing out the supported schemes. |
| 5xx | UK.OBIE.UnexpectedError | An error code that can be used, when an unexpected error occurs. The ASPSP must populated the message with a meaningful error description, without revealing sensitive information. |
Optional Fields
In objects where the value for an optional field is not specified, the field must be excluded from the JSON payload.
In objects where an array field is defined as having 0..n values, the array field must be included in the payload with an empty array.
{
"Name": "", // Incorrect. Exclude the Name field from the payload.
"Age": 0, // Incorrect. 0 should not be used to indicate an undefined age.
"CreditorAccount": {}, // Incorrect. Exclude the CreditorAccount field.
"Balances": [] // Correct. This is the method of indicating an empty array. Do not suppress the Balance field.
}
Links
The Links section is mandatory and will always contain absolute URIs to related resources,
The "Self" member is mandatory.
For example:
"Links": {
"Self": "https://api.alphabank.com/open-banking/v1.0/payments/58923"
}
Where an API provides a paginated response, the Links element must also contain the members First, Prev, Next and Last.
For example:
"Links": {
"Self": "http://example.com/articles?page[number]=3&page[size]=1",
"First": "http://example.com/articles?page[number]=1&page[size]=1",
"Prev": "http://example.com/articles?page[number]=2&page[size]=1",
"Next": "http://example.com/articles?page[number]=4&page[size]=1",
"Last": "http://example.com/articles?page[number]=13&page[size]=1"
}
Meta
The Meta section is mandatory, but may be empty. An optional member is "TotalPages" which is specified as an integer (int32) and shows how many pages of results (for pagination) are available.
For example:
"Meta": {
"TotalPages": 13
}
Enumerations
Basics
Some fields have a fixed set of enumerations - in this case:
- The enumerations with a fixed set of values are defined as part of the specification.
- The enumerations with a fixed set of values are defined in the corresponding Swagger file.
However, there are certain fields that do not have a fixed set of enumerations and may be extended by ASPSPs - in this case:
- The enumerations are managed by namespacing the values.
- The enumerations are not documented as part of the core standard but are listed out separately in OB Developer Zone and in the ASPSP's developer portals.
When extending a namespaced enumeration:
- ASPSPs must not publish an ASPSP-specific enumerated value where a generic OBIE defined enumerated value may be used.
- ASPSPs must place such values in a namespace consisting of their two-letter country code (ISO 3166-1 Alpha-2 code), followed by a full-stop, followed by their name. e.g.
UK.Barclays.PingItKE.Safaricom.M-Pesa
Common Namespaced Enumerations
The following namespaced enumerations are used across all the standards.
Account/SchemeName
This field is used to identify the type of Identification used to identify an account.
The enumerated values specified by Open Banking are documented in Developer Zone and will be prefixed by UK.OBIE e.g.:
UK.OBIE.SortCodeAccountNumber
UK.OBIE.IBAN
UK.OBIE.PAN
UK.OBIE.Paym
UK.OBIE.BBAN
As a special case and in order to minimize disruption between versions of the standard, a TPP may specify only these values without namespacing:
SortCodeAccountNumber(instead ofUK.OBIE.SortCodeAccountNumber)IBAN(instead ofUK.OBIE.IBAN)PAN(instead ofUK.OBIE.PAN)
The use of these non-namespaced values may be discontinued in a future version of this standard.
In ASPSP generated responses, an ASPSP must always respond with fully namespaced values.
Agent/SchemeName
This field is used to identify the type of Identification used to identify an agent.
The enumerated values specified by Open Banking are documented in Developer Zone and will be prefixed by UK.OBIE e.g.:
UK.OBIE.BICFI
As a special case and in order to minimize disruption between versions of the standard, a TPP may specify only these values without namespacing:
BICFI(instead of BICFIUK.OBIE.BICFI)
The use of these non-namespaced values may be discontinued in a future version of this standard.
In ASPSP generated responses, an ASPSP must always respond with fully namespaced values.
Usage Examples
The usage examples for the individual APIs are documented in their respective pages.
This section provides usage examples for some repeating patterns that are used by multiple resources.
Pagination Flows
The example below illustrates how an ASPSP may return a paginated response.
Request
GET /accounts/22289/transactions HTTP/1.1 Authorization: Bearer Az90SAOJklae x-fapi-financial-id: OB/2017/001 x-fapi-customer-last-logged-time: Sun, 10 Sep 2017 19:43:31 GMT x-fapi-customer-ip-address: 104.25.212.99 x-fapi-interaction-id: 93bac548-d2de-4546-b106-880a5018460d Accept: application/json
Paginated Resource Response
HTTP/1.1 200 OK
x-fapi-interaction-id: 93bac548-d2de-4546-b106-880a5018460d
Content-Type: application/json
{
"Data": {
...
},
"Links": {
"Self": "https://api.alphabank.com/open-banking/v1.0/accounts/22289/transactions/",
"Last": "https://api.alphabank.com/open-banking/v1.0/accounts/22289/transactions?pg=20",
"First": "https://api.alphabank.com/open-banking/v1.0/accounts/22289/transactions/",
"Next": "https://api.alphabank.com/open-banking/v1.0/accounts/22289/transactions?pg=2"
},
"Meta": {
"TotalPages": 20,
"FirstAvailableDateTime": "2017-05-03T00:00:00+00:00",
"LastAvailableDateTime": "2017-12-03T00:00:00+00:00"
}
}
The TPP may follow the links provided in the Links section of the payload to navigate to the first, last, next and previous pages:
Request Next Page of Results
GET /accounts/22289/transactions?pg=2 HTTP/1.1 Authorization: Bearer Az90SAOJklae x-fapi-financial-id: OB/2017/001 x-fapi-customer-last-logged-time: Sun, 10 Sep 2017 19:43:31 GMT x-fapi-customer-ip-address: 104.25.212.99 x-fapi-interaction-id: 93bac548-d2de-4546-b106-880a5018460d Accept: application/json
Paginated Resource Response
HTTP/1.1 200 OK
x-fapi-interaction-id: 93bac548-d2de-4546-b106-880a5018460d
Content-Type: application/json
{
"Data": {
...
},
"Links": {
"Self": "https://api.alphabank.com/open-banking/v1.0/accounts/22289/transactions?pg=2",
"Last": "https://api.alphabank.com/open-banking/v1.0/accounts/22289/transactions?pg=20",
"First": "https://api.alphabank.com/open-banking/v1.0/accounts/22289/transactions/",
"Next": "https://api.alphabank.com/open-banking/v1.0/accounts/22289/transactions?pg=3",
"Prev": "https://api.alphabank.com/open-banking/v1.0/accounts/22289/transactions?pg=1"
},
"Meta": {
"TotalPages": 20,
"FirstAvailableDateTime": "2017-05-03T00:00:00+00:00",
"LastAvailableDateTime": "2017-12-03T00:00:00+00:00"
}
}
Error Flows
This section provides some examples of error scenarios and the expected outputs.
Missing or Expired Access Token
This flow assumes that the following Steps have been completed successfully:
- Step 1: Request Account Information
- Step 2: Setup Account Request
- Step 3: Authorise Consent
The AISP attempts to provide an expired or missing access token to the ASPSP in an attempt to Request Data
Incomplete or Malformed Request Payload
This flow assumes that the following Steps have been completed successfully:
- Step 1: Request Account Information
- Step 2: Setup Account Request
- Step 3: Authorise Consent
The AISP provides a malformed request to the ASPSP in an attempt to setup an Account Request.
Missing or Invalid Access Token Scope
This flow assumes that the following Steps have been completed successfully:
- Step 1: Request Account Information
- Step 2: Setup Account Request
- Step 3: Authorise Consent
The AISP provides a (valid) access token which does not have a valid scope (or link to the correct Permissions) to Request Data
Sudden Burst of API Requests
This flow assumes that the following Steps have been completed successfully:
- Step 1: Request Account Information
- Step 2: Setup Account Request
- Step 3: Authorise Consent
The AISP provides a (valid) access token which is used to generate a burst of multiple requests to retrieve an Accounts resource.
The ASPSP may optionally choose to return a 429 Response
Failed Authorisation Consent
This flow assumes that the following Steps have been completed successfully:
- Step 1: Request Account Information
- Step 2: Setup Account Request
The Step 3: Authorise Consent Flow fails to succeed due to the PSU providing invalid credentials to the ASPSP, resulting in no Authorization Code being generated.
JSON Error Response
POST /domestic-payment-consents HTTP/1.1
Authorization: Bearer 2YotnFZFEjr1zCsicMWpAA
x-idempotency-key: FRESCO.21302.GFX.20
x-jws-signature: TGlmZSdzIGEgam91cm5leSBub3QgYSBkZXN0aW5hdGlvbiA=..T2ggZ29vZCBldmVuaW5nIG1yIHR5bGVyIGdvaW5nIGRvd24gPw==
x-fapi-financial-id: OB/2017/001
x-fapi-customer-last-logged-time: Sun, 10 Sep 2017 19:43:31 GMT
x-fapi-customer-ip-address: 104.25.212.99
x-fapi-interaction-id: 93bac548-d2de-4546-b106-880a5018460d
Content-Type: application/json
Accept: application/json
{
"Data": {
"Initiation": {
"EndToEndIdentification": "FRESCO.21302.GFX.20",
"InstructedAmount": {
"Amount": "165.88",
"Currency": "GBP"
},
"CreditorAccount": {
"SchemeName": "MyImaginaryScheme",
"Identification": "08080021325698",
"Name": "ACME Inc",
"SecondaryIdentification": "0002"
},
"RemittanceInformation": {
"Reference": "FRESCO-101",
"Unstructured": "Internal ops code 5120101"
}
}
},
"Risk": {
"PaymentContextCode": "EcommerceGoods",
"MerchantCategoryCode": "5967",
"MerchantCustomerIdentification": "053598653254",
"DeliveryAddress": {
"AddressLine": [
"Flat 7",
"Acacia Lodge"
],
"StreetName": "Acacia Avenue",
"BuildingNumber": "27",
"PostCode": "GU31 2ZZ",
"TownName": "Sparsholt",
"CountySubDivision": [
"Wessex"
],
"Country": "UK"
}
}
}
HTTP/1.1 400 Bad Request
x-jws-signature: V2hhdCB3ZSBnb3QgaGVyZQ0K..aXMgZmFpbHVyZSB0byBjb21tdW5pY2F0ZQ0K
x-fapi-interaction-id: 93bac548-d2de-4546-b106-880a5018460d
Content-Type: application/json
{
"Code": "400 BadRequest",
"Id": "2b5f0fb2-730b-11e8-adc0-fa7ae01bbebc",
"Message": "Invalid request parameters.",
"Errors": [
{
"ErrorCode": "UK.OBIE.Field.Missing",
"Message": "Instructed identification is missing",
"Path": "Data.Initiation.InstructionIdentification",
"Url": "<url to the api reference for Payment Inititaion API>"
},
{
"ErrorCode": "UK.OBIE.Unsupported.Scheme",
"Message": "Scheme name supplied is not supported",
"Path": "Data.Initiation.CreditorAccount.SchemeName",
"Url": "<url to the online documentation referring supported scheme names>"
}
]
}
© Open Banking Limited 2019 | https://www.openbanking.org.uk/open-licence | https://www.openbanking.org.uk
.png?version=1&modificationDate=1536313131811&cacheVersion=1&api=v2&width=698&height=400)
.png?version=1&modificationDate=1536313131693&cacheVersion=1&api=v2&width=738&height=342)
.png?version=1&modificationDate=1536313131943&cacheVersion=1&api=v2&width=700&height=400)
.png?version=1&modificationDate=1536313132292&cacheVersion=1&api=v2&width=700&height=473)